Services
NATIONAL-LEVEL CYBER DRILL
A 5-day event that prepares security units to respond quickly and efficiently to cyber threats and incidents targeting national critical infrastructure. Participants will engage in real-life cyber incident simulations, testing their defensive abilities in real-time.
Our simulation scenarios are tailored to meet the exact needs of any government agency or national security unit.
REINFORCE YOUR CYBER DEFENSE – Practice key defensive skills in lifelike scenarios of emergency.
EMPOWER SECURITY UNITS – Work together to build trust, teamwork, and camaraderie.
PROTECT YOUR NATION – Improve strategic decision making, communication, and effectiveness under stress.
REAL-LIFE SIMULATION SCENARIOS
Our simulation scenarios meet the exact needs of any government agency or national security unit.
Here are some examples of the scenarios we offer:
Scenario 1 – Total Black Out
A nation-state actor infiltrates another country’s power grid systems. Once inside the system, they cause a blackout across the entire country.
CONSEQUENCES
Large-scale power outages affecting hospitals, public transportation, and essential services.
Potential for casualties if emergency services are unable to respond in time.
Scenario 2 – Back To the Stone Age
A nation-state actor targets the country’s major telecommunication providers,
disrupting communication infrastructure and causing network outages.
CONSEQUENCES
Disruption of communication services including internet, mobile, and landline connectivity.
Impact on emergency services that rely on Telecommunication networks.
Scenario 3 – Economic Downfall
Nation-state cybercriminals infiltrate the central bank’s systems,
manipulating data to create financial instability, altering balances and transaction records.
CONSEQUENCES
Coordinated misinformation campaign to amplify the impact of the attack and sow confusion.
Deflates the Local Currency and crashes the stock market.
Scenario 4 – Blackbyte Espionage
Nation-state actors engage in a large-scale intellectual property theft and
espionage campaign at government agencies and corporations.
CONSEQUENCES
Loss of sensitive data, including military secrets and proprietary technologies.
Economic impact due to the loss of competitive advantage in various sectors
Scenario 5 – Healthcare Fire Sale
Nation-state attacker deploys ransomware targeting a nation’s healthcare systems,
encrypting patient records and demanding a large ransom.
CONSEQUENCES
Disruption of medical services, potential patient harm, financial losses, and public outcry.
Revels sensitive information regarding citizens to other nations.
PENETRATION TESTING SERVICES
As most operations within an organization today are significantly dependent on the well-being of IT systems, it is crucial for these to count of solid security controls. Determining how effective these are is key to find points of improvement and make tweaks to better protect your assets. As a result, thoroughly testing your entities’ security systems periodically must become a must in their agendas.
Penetration Testing both measures the degree of quality of their security systems and detects your organizations’ particular vulnerabilities. Outsourcing pen testing services to expert companies to effectively seal your business’ gaps and successfully manage risks is an investment that pays off.
We apply the following pen-testing methods to guarantee the most accurate results:
CYBERPRO.AI counts different testing modalities, allowing our testers to dissect and moreover dig deeper into different aspects of the systems, and furthermore, providing a more accurate and thorough assessment of your organization’s potential vulnerabilities.
BLACK-BOX
Black Box:
Black box testing treats the software without any knowledge of internal implementation. Black box testing can be regarded as an opaque and closed box. “Opaque” means we know nothing about its inside, and “closed” means we do not have the access to modify the source codes. Black box aims at examining the functionality of an application without diving into its internal structure.
GREY-BOX
Grey Box:
Grey box testing is the combination of black box testing and white box testing, aiming at identifying defects due to wronged structure or application use. It can be regarded as a clear and closed box because a tester know the details in the codes but do not have the access to change them. It takes the straightforward technique of black-box testing and combines it with the code-targeted systems in white-box testing.
WHITE-BOX
White Box:
As the tester performs White Box testing, they have access to the internal data structures, algorithms and codes. The tester can not only see the source codes but also manipulate the codes as part of testing process.
CYBERPRO.AI counts on top-notch expertise and to perform penetration testing on a broad range of areas within the IT spectrum
CYBERPRO.AI has successfully provided pen-testing services across different sectors including military organizations and private and public companies.
You will be provided with a complete view and thorough reporting on your organizations’ vulnerabilities with detailed insight on security threats and how to prioritize remediation and closure of existing gaps within your system. Assessing risks and threats before breaches actually take place will also help you avoid financial distress. CYBERPRO.AI will take the lead and guide you away from these drawbacks.
TABLETOP EXERCISES
We are on a mission to build strong, resilient, and cyber aware organizations. More and more organizations are being targeted by cyber threats, and as these attacks become more sophisticated, organizations need better, more effective incident response plans to keep their valuable data safe.
Regular Tabletop Exercises run separate Management and Technical exercises. CYBERPRO.AI Global believes that these teams must work together to provide organizations with an optimal incident response plan. Introducing the CYBERPRO.AI Global TTX for management and tech teams:
The CYBERPRO.AI tabletop exercise offers unique benefits compared to regular Tabletop Exercises.
Synergize management and tech teams for improved joint incident response.
Streamline roles and responsibilities across the whole organization.
Generate new ideas and approaches to face cyber incidents.
Optimize plans and procedures for a more resilient cyber strategy.
Stage 1 – Assess Your Strengths And Weaknesses
Assess current policies, procedures and materials thoroughly to gain insights into potential weaknesses.
Launch a phishing campaign across all departments, using our proprietary Cywareness
to provide the organization with a general cyber awareness score.
Sit down with team members, engaging all personnel and the relevant teams with the TTX.
Stage 2 – Increase Your Knowledge And Awareness
For Management Teams
Assess decision-making under conditions of uncertainty and stress.
Evaluate information-sharing processes within the organization.
Verify the Incident Response Plan’s fit for purpose.
Manage the transition from Incident Response to Business Continuity.
For Technical Teams
Assess technical competency and knowledge of the IR/SOC teams.
Measure coverage as defined by BIA and policies.
Analyze IR and BC processes, their effectiveness and timeliness.
Train the technical teams within the organization with immersive gamified Cyber Range, CYWARIA.
Stage 3 – Improve Your Processes And Strategies
Provide an in-depth report that presents our findings (individual teams and collective).
Run workshops and talks to outline a roadmap to a
new resilient incident response plan with updated policies and procedures.
FORENSIC SERVICES
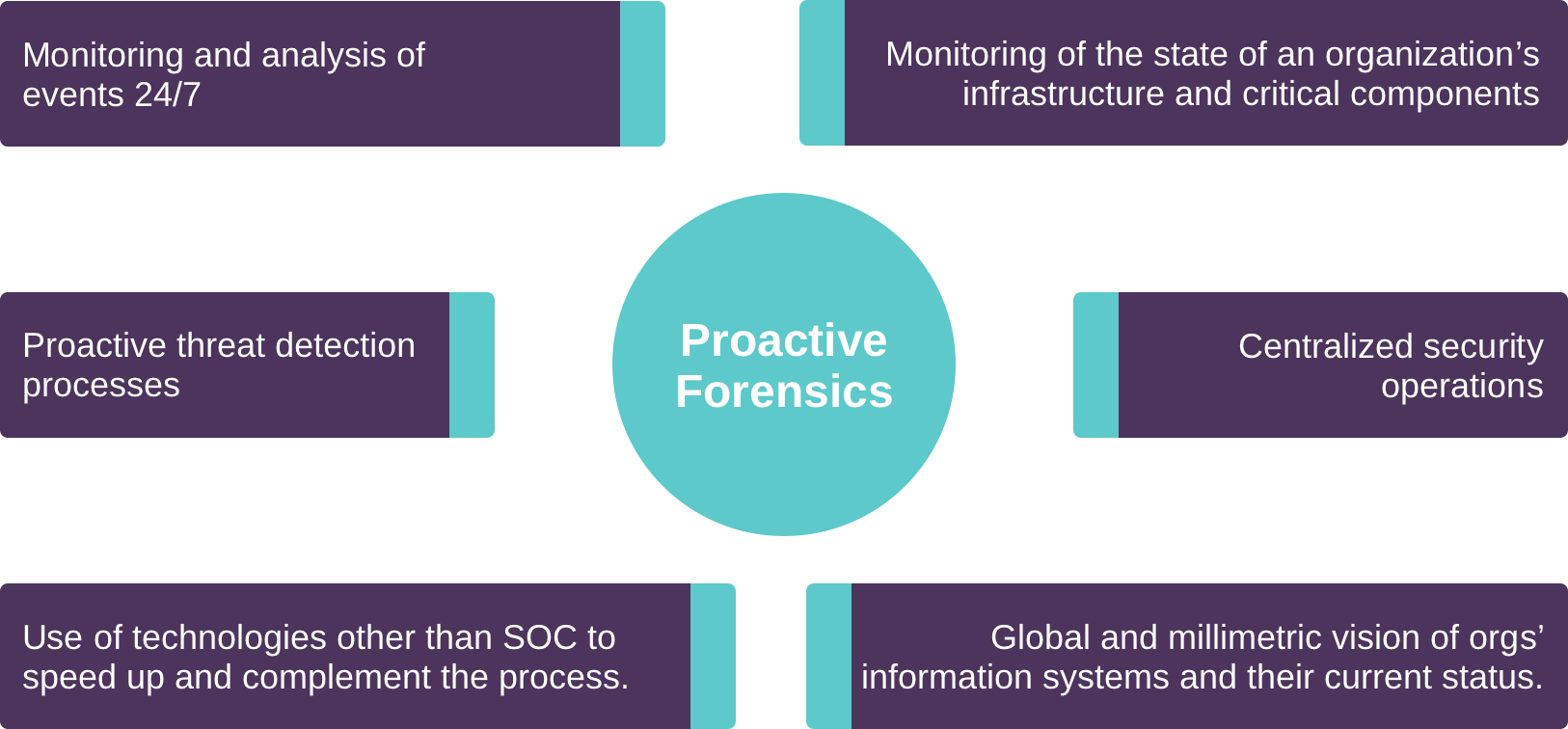
Understanding that the cyber threats organizations and systems face are numerous and can pertain any stage and aspect of their structure, CYBERPRO.AI also offers additional proactive and reactive forensic services. If your organization is victim of any sort of cyberattack, CYBERPRO.AI will take the lead in dissecting it, understanding its source, identifying recovery potential, and furthermore providing with strong insight on prevention strategies and actions. Our team of specialists has designed them to adapt to your organization’s circumstances, requirements and needs. If your organization has shown an incident, you CYBERPRO.AI will come and take over the challenge.
CYBERPRO.AI’s proactive and reactive services can be particularly tailored to your companies needs.
REMOTE / ON PREMISE
PERIODIC / SPECIFIC
3rd PARTY PRODUCTS & SERVICES
REMOTE / ON PREMISE
PERIODIC / SPECIFIC
3rd PARTY PRODUCTS & SERVICES
Take a look at our list of proactive and reactive services!
Proactive
Forensics
Web
Forensics
Reactive
Forensics
Incident
Response
Malware
Detection
SOC AS A SERVICE
CYBERPRO.AI’s SOC Support Service as is network to help professionals dedicated to data protection by monitoring and reporting the state of their organizations’ systems continuously: 24 h a day, and 7 days a week, all year long. SOCs detect and prevent cyber threats from harming an organization’s system through tailored processes and technology. With SOCs, organizations seek to speed up their attack detection and mitigation processes. Nonetheless, running SOCs efficiently is a meticulous and somewhat complex task, requiring investment in money, skills, and time, one of today’s most treasured assets.
Considering the level of complexity behind SOCs, CYBERPRO.AI has carefully crafted a high-end SOC service. Backed by a team of top-notch, in house specialists, our service is guaranteed to speedily and timely identify, analyze, and treat cyber-related incidents. We will boost your organization’s threat detection and management abilities to heights, and more importantly, protect your backbone assets. We offer a customizable solution of the highest quality in order to adjust to our clients’ most specific needs. CYBERPRO.AI is the ideal partner and will drive your company to success!
Our SOC Support Service includes:
CYBERPRO detailed pen tests for Internal and External Networks look forward to detecting weak spots which may put personal and financial information at risk in order to seal the existing gaps and further voiding potential threats. While internal network pen testing helps measure how much an attacker can achieve once they accessed the network, external testing evaluates perimeter security and identifies weaknesses in web, mail and FTP servers.
As Web Applications are highly prone to undergo cyber incidents, thorough testing on their frameworks, APIs, or coding are vital in order to evaluate to what degree these are secure. Our pen testing services will ensure the risks these are exposed to are mitigated.
CYBERPRO’s Cloud Pen Testing will lead to finding weaknesses withing a system hosted on a cloud provider. The testing will provide you with a better understanding of the status of your cloud, reporting on any misconfiguration and advice on how to better secure your cloud systems.
CYBERPRO pen tests for mobile application cover a wide range of aspects of it, including mobile platform internals, app development lifecycles, reverse engineering and tampering, software protection, session management, access controls, cryptography, error handling and data protection, among other key factors.
Effectively securing your network is key to safeguard an organization’s vital assets. These must be equipped with controls in order to detect and mitigate malicious moves or potential threats. Therefore, CYBERPRO’s services cover pen tests for a vast range of areas withing the Network Security field, ranging from wireless networks to maintenance processes.
CYBERPRO’s Secure Code Reviews will allow us to identify security-related weaknesses of an application’s source code. The reviews will provide developers insight on reshaping the source code in order to make it more secure.
Web Application Firewalls act as safety nets, offering protection from attacks against vulnerable web apps, and are key to secure a companies’ web environment. Performing evasion techniques On WAFs will allow the identification of loopholes in the firewall and lead to design better WAF strategies.
CYBERPRO’s pen tests on ERP Systems are geared towards locating security gaps and issues coming from misconfigurations, default installations, and other sources. Security configurations of ERP systems are usually left to default, which may lead to potential weaknesses and exposure to vulnerabilities. Pen testing will allow to discover and strengthen these systems’ security configurations.
CYBERPRO’s pen tests on ERP Systems are geared towards locating security gaps and issues coming from misconfigurations, default installations, and other sources. Security configurations of ERP systems are usually left to default, which may lead to potential weaknesses and exposure to vulnerabilities. Pen testing will allow to discover and strengthen these systems’ security configurations.
CYBERPRO’s pen tests on ERP Systems are geared towards locating security gaps and issues coming from misconfigurations, default installations, and other sources. Security configurations of ERP systems are usually left to default, which may lead to potential weaknesses and exposure to vulnerabilities. Pen testing will allow to discover and strengthen these systems’ security configurations.
CYBERPRO’s pen tests on ERP Systems are geared towards locating security gaps and issues coming from misconfigurations, default installations, and other sources. Security configurations of ERP systems are usually left to default, which may lead to potential weaknesses and exposure to vulnerabilities. Pen testing will allow to discover and strengthen these systems’ security configurations.
CYBERPRO’s pen tests on ERP Systems are geared towards locating security gaps and issues coming from misconfigurations, default installations, and other sources. Security configurations of ERP systems are usually left to default, which may lead to potential weaknesses and exposure to vulnerabilities. Pen testing will allow to discover and strengthen these systems’ security configurations.
CYBERPRO’s pen tests on ERP Systems are geared towards locating security gaps and issues coming from misconfigurations, default installations, and other sources. Security configurations of ERP systems are usually left to default, which may lead to potential weaknesses and exposure to vulnerabilities. Pen testing will allow to discover and strengthen these systems’ security configurations.
